Which Technology Can Be Used to Protect Voip Against Eavesdropping
Another way to combat VoIP eavesdropping is to constantly update your session border controllers SBCs. Updating your SBCs is one of the technologies that you can use to protect VoIP against eavesdropping.

How To Protect Voip Services Against Sip Hacking An Expert Guide
You can protect VoIP from eavesdropping by updating your SBCs.

. Many advanced technologies such as VoIP streaming video and electronic conferencing require. There are multiple task types that may be available in this quiz. What three best practices can help defend against social engineering attacks.
Your SBC requires the same kind of management regimen you should already have in place for your other security tools. Additionally consider installing intrusion detection and prevention systems to monitor and filter unauthorized VoIP traffic. You can protect VoIP from eavesdropping by updating your SBCs.
Which technology can be used to protect VoIP against eavesdropping. During VoIP eavesdropping a hacker or sniffer will infiltrate the network through a compromised VoIP device or via part of the VoIP infrastructure such as a switch cable or internet and listen in on unencrypted VoIP calls. Which technology can be used to protect VoIP against eavesdropping.
You should update the Session border controllers just like you do for antivirus software. Quizzes allow for partial credit scoring on all item types to foster Continue. Which technology can be used to protect VoIP against eavesdropping.
Encrypted voice messages strong authentication SSH ARP. To effectively defend against VoIP eavesdropping businesses need to take a holistic approach to cybersecurity. IP private branch exchange PBX using minimal services so that the hardware can only power the PBX software.
Which technology can be used to protect VoIP against eavesdropping. Contact us 00800 33 090300. Update the Session border controllers the same way you update antivirus applications.
You should update the Session border controllers just like you do for antivirus software. To effectively defend against VoIP eavesdropping businesses need to take a holistic approach to cybersecurity. By doing so youll be updating your VoIPs antivirus software which means your systems are better protected from constantly evolving cyberthreats.
Which technology can be implemented as part of an authentication system to. This includes enforcing policies deployment and security practices that will keep malicious agents out of your network. After separating your networks set up a firewall for your VoIP network that can identify signs of attack.
Many of the security measures widely used today to protect other plain text applications from telnet and FTP to Web e-mail and instant. In case of suspicion please choose a means of communication outside the affected area. Which technology can be used to protect VoIP against eavesdropping.
Lightweight Directory Access Protocol lookup and signaling and management protocol. Which technology can be used to protect VoIP against eavesdropping. Cybersecurity Essentials 11 Final Quiz Answers 100 2018 Quiz Instructions This quiz covers all of the content in Cybersecurity Essentials 11.
Voice over IP VoIP eavesdropping is an example of a passive eavesdropping attack. Encrypted voice messages strong authentication SSH ARP. Build a hardened VoIP network.
This will act as your first line of defense against eavesdroppers. Which technology can be used to protect VoIP against eavesdropping. It is designed to test the skills and knowledge presented in the course.
Which technology can be used to protect VoIP against eavesdropping. Which Technology Can Be Used To Protect Voip Against Eavesdropping. Implement Session Border Controllers SBCs.
We will answer your questions about anti-eavesdropping and protection against bugging in your company.
![]()
Voip Hacking How To Protect Your Phones From Cybercrime Iconic It

Which Technology Can Be Used To Protect Voip Against Eavesdropping Flashmob Computing

Hp Laserjet 9000 9040 9050 Series Maintenance Kit 110v Includes Fuser Assembly 7 Feed Separa By Hp 349 99 H Hewlett Packard Packard Zebra Label Printer

Encryption What Is End To End Encryption For Your Voip Dynamix

How To Ensure Voip Security For Your Business

Which Technology Can Be Used To Protect Voip Against Eavesdropping Flashmob Computing

Voip Security That Needs To Be Controlled To Flawless Voip Services

What Is Voip The Complete Guide To Voice Over Ip Calling

Protecting Against Cyber Threats When Using Voip
What Are Eavesdropping Attacks How To Prevent Them Verizon Business

Voip Security How Secure Is Your Voip Cyphere
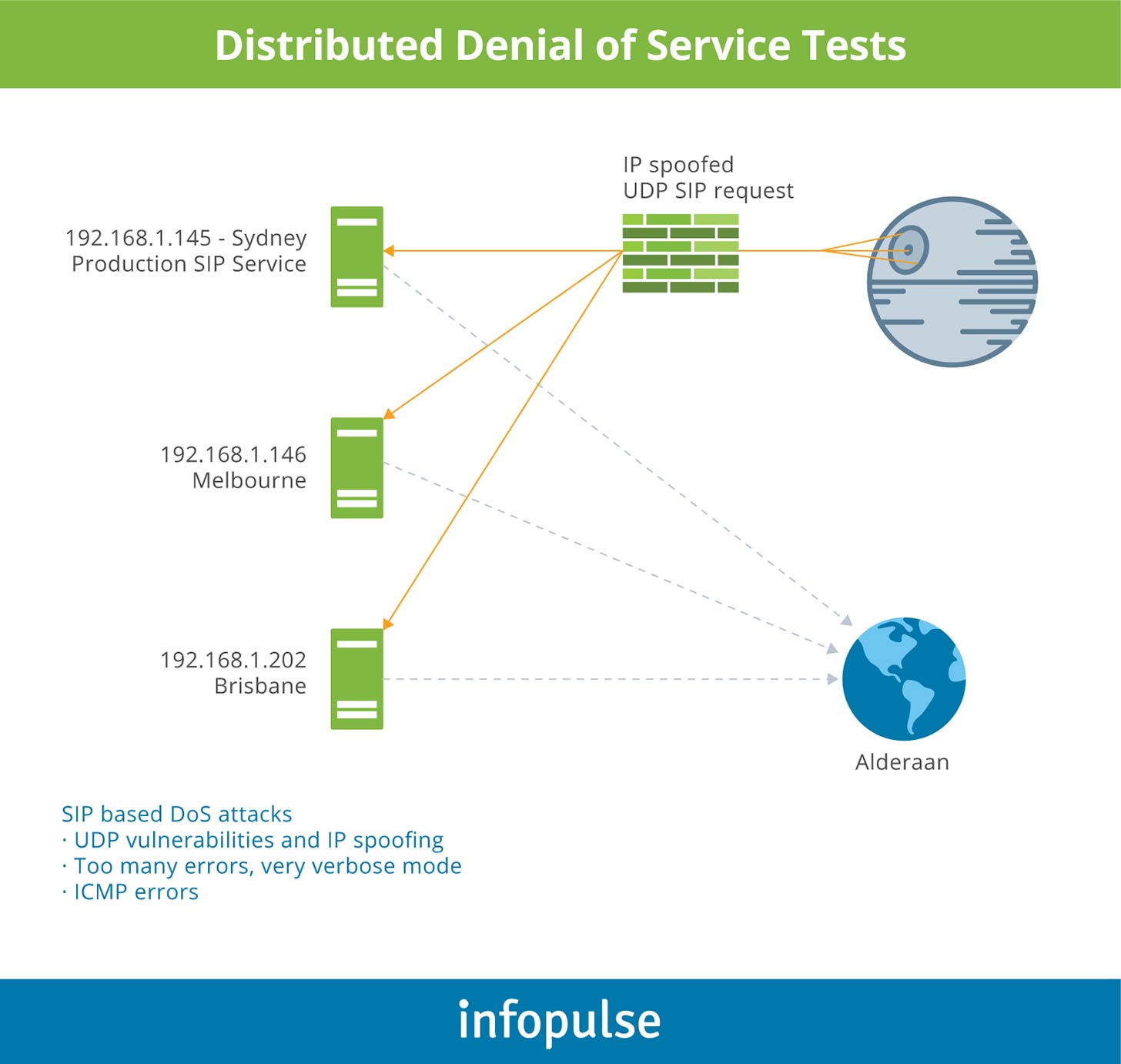
How To Protect Voip Services Against Sip Hacking An Expert Guide

Which Technology Can Be Used To Protect Voip Against Eavesdropping Flashmob Computing

Facebook Is Bringing End To End Encryption To Messenger Calls And Instagram Dms Techcrunch

How Secure Is Voip Understanding Voip Security Risks Issues Threats Businesstechweekly Com

Voip Security How Secure Is Your Voip Cyphere

How Secure Is Voip Vs Landline Voip Security Ooma Canada

Iphone Tricks Iphone Hacks Iphone Camera Hard Disk

The Top Voip Security Risks And How You Can Protect Your Business
Comments
Post a Comment